Release 3 (8.1.7)
A83720-01
Library |
Product |
Contents |
Index |
| Oracle8i
Oracle Servlet
Engine User's Guide Release 3 (8.1.7) A83720-01 |
|
This chapter contains a series of operations designed to be helpful in setting up the HTTP security for the servlet engine. The topics we cover are the following:
Before you define and program the security settings in the OSE, you must be proficient at setting up and manipulating the JNDI structure. Verify your knowledge against the following checklist:
If you are unsure of any of the above topics, review the diagrams and examples describing how the OSE works with the JNDI namespace and how Web browsers interact with the OSE. A link follows each topic to a specific discussion. A complete example list is located in Appendix B, "Examples".
After you learn the basic security set up in this chapter, you can safely change the configuration of your Web service security from the default set up.
In HTTP security, access to a protected resource is composed of two parts: authentication of valid credentials and authorization of the user. Authentication is the validation of submitted credentials establishing that a user is known and validated by the system. Authorization is the determination of whether an authorized user is allowed to perform the requested action.
There are four stages to declare when establishing security measures:
root of the servlet context.
Use these steps to ensure the correct base information is in use defining HTTP security for your Web resources. Without any one of these steps, security will either be non-existent or will deny access to protected resources.
A principal is a generic term for either a user or a group. The realm is an object in the service, which contains the declared principals. Figure 8-1 shows the position of the realm object at the top level of the Web service, at the same level as the config object for the service.
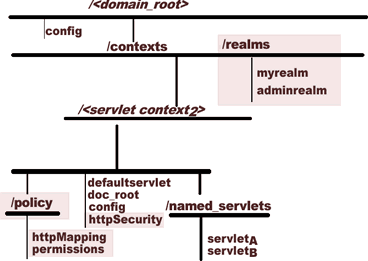
Groups contain other principals (users or other groups). Individual members of a group inherit the permission of the group object.
Users are single objects. Unlike a group, there are no subsets of other principals belonging to a user.
Each realm defines a separate set of principals. The realm and its implementation are core to all of HTTP Security. There can be multiple realms within a service. The realm is the source of:
Because the realm is the source of all principals, it also plays a key role in:
By default, there are three implementations of realms, named in HTTP Security:
These names are just shortcuts. When instantiating the realm, use the appropriate name when declaring the realm class in the JNDI namespace.
The DBUSER realm is a principal definition derived from the users and roles defined within the database. There are several implications.
create user "joe" identified by welcome;
then the username would be joe, in lowercase.
You set the security levels with the realm command, using the different flags and options. You can see the complete definition of all valid realm uses in the Oracle Java Tools Reference. To see a list of the different choices, execute the realm command from the session shell.
$ realm usage: realm realm list -d <webServiceRoot> realm echo [0|1] realm secure -s <servletContextPath> realm map -s <servletContextPath> [- add|remove <path>] [-scheme <auth>:<realm>] realm publish -d <webServiceRoot> [- add|remove <realmName>] [-type RDBMS | DBUSER | JNDI] realm user -d <webServiceRoot> -realm <realmName> [- add|remove <userName> [-p <user password>]] realm group -d <webServiceRoot> -realm <realmName> [- add|remove <groupName> [-p <group password>]] realm parent -d <webServiceRoot> -realm <realmName> [-group <groupName> [- add|remove <principalName>]] [-query <principalName>] realm perm -d <webServiceRoot> -realm <realmName> -s <servletContextPath> -name <principalName> [-path <path> (+|-) <permList>]
Underscoring its central role, realm is the start of all security commands in the shell. The following sections depict example commands creating and managing realms from the shell.
To create a RDBMS realm, type:
realm publish -w /myService -add testRealm -type RDBMS
For JNDI and DBUSER, use those titles as the type argument.
To remove a realm, type:
realm publish -w /myService -remove testRealm
Realm declarations reside in the JNDI namespace. Deploying customized realms, once written, requires only slight customization of the namespace entry.
To publish a custom realm, type:
realm publish -w /myService -add testRealm -classname foo.bar.MyRealm
To create a user, type:realm user -w /myService -realm testRealm1 -add user1 -p upswd1
To create a group, type:
realm group -w /myService -realm testRealm1 -add group1 -p gpswd1
In either of the above commands, if the password is left blank, the principal name is used instead.
To delete a user, type:
realm user -w /myService -realm testRealm1 -remove user1
To delete a group, type:
realm group -w /myService -realm testRealm1 -remove group1
To list users of a realm, type:
realm user -w /myService -realm testRealm1
To list groups of a realm, type:
realm group -w /myService -realm testRealm1
To add a principal to a group, type:
realm parent -w /myService -realm testRealm -group group1 -add user1
To remove a principal from a group, type:
realm parent -w /myService -realm testRealm -group group1 -remove user1
To list principals within a group, type:
realm parent -w /myService -realm testRealm -group group1
To query which groups a principal is a member of, type:
realm parent -w /myService -realm testRealm -q user1
(All realms do not support this query option.)
|
Note: Not all realms support editing principals. For example, DBUSER realms do not support any principal manipulation. |
If a service has any realms declared, they are located in a realms sub-context of the service. If it is a JNDI realm, there is additional sub-contexts within the realms context that contain its principal declarations.
If /realms is removed, all realm definitions are removed along with it. However any external resources (such as table entries) would remain. Using the session shell realm tool is much safer for efficient realm management.
Removing subcontexts of realms can affect any JNDI type realms. The RDBMS realm is defined to use the following tables:
OSE HTTP security resource protection is local to the servlet context. To declare a resource protected, two pieces of information must be supplied, embodied in a protection scheme. A scheme is of the form:
<authType>:<realmName>
There are two valid authentication types:
Although Digest is far more secure than Basic, not all browsers support it. From looking at typical installations, IE5 supports it; Netscape 4.7 does not.
You can also declare resources not to be protected. This is useful when the servlet context root is to be protected. However, when the root is protected, the error pages, being part of the tree, are also protected. Delivering an error page is part of the authentication process. If the error page is protected, cycles develop, and the desired behavior is not observed.
Instead of letting the error page default as part of the tree, explicitly declare the error pages as not being protected. Use a protection scheme of <NONE>. For example:
realm map -s /myService/contexts/myContext -a /system/* -scheme <NONE>
realm map -s /myService/myService/contexts/myContext -a /* -scheme basic:testRealm1
The protected path is local to the servlet context. Internally, that path is normalized, enabling stable, predictable patterns for matching. This may cause the internal representation to differ from the original path used to create the protection scheme. HTTP Security will use the longest, most exact match possible when trying to apply the protection rules.
Protecting paths to resources with protection schemes:
realm map -s /myService/contexts/myContext -a /doc/index.html -scheme basic:testRealm1
realm map -s /myService/contexts/myContext -a /doc -scheme basic:testRealm2
realm map -s /myService/contexts/myContext -a /doc/* -scheme basic:testRealm3
When declarations are made, as shown in the previous example, the paths are matched to realms as in the following examples:
/doc/index.html -> testRealm1
/doc/foo -> testRealm3
/doc -> testRealm2
/doc/ -> testRealm2
/doc/index -> testRealm3
To remove the protection of a path, type:
realm map -s /myService/contexts/myContext -r /doc/index.html
To list all protected paths within a servlet context, type:
realm map -s /myService/contexts/myContext
To explicitly declare a path not to be protected, type:
realm map -s /myService/contexts/myContext -a /system/* -scheme <NONE>
To list all protected paths within a servlet context, type:
realm map -s /myService/contexts/myContext
The JNDI entry for protection mappings is located in a subdirectory, policy, of the servlet context. Within that sub-context is an entry, httpMapping, which creates the object responsible for handling the security servlet protection mapping. By default, this object is used as an index into the JAVA$HTTP$REALM$MAPPING$ table. The HTTP realm mapping table contains all the mapped paths. Simple JNDI entry manipulation can introduce a customized version of HttpProtectionMapping.
Permissions are the most involved of all HTTP Security declarations because they tie domain-scoped entities with servlet context-scoped entities and reside in the servlet context themselves.
A permission declaration consists of several pieces:
Given all the pieces that are being tied into one permission declaration, it is easy to see why these are the most complicated declarations.
Of those pieces, only the HTTP actions have not been talked about yet. HTTP security permissions concern only valid HTTP request methods: GET, POST, PUT, DELETE, HEAD, TRACE, OPTIONS.
To declare a granted permission on /foo/index.html for user1 for GET and POST, type:
realm perm -w /myService -realm testRealm1 -s /myService/contexts/myContext -n user1 -u /foo/index.html + get,post
To declare a denied permission on /foo/* for user1 for PUT and DELETE, type:
realm perm -w /myService -realm testRealm1 -s /myService/contexts/myContext -n user1 -u /foo/* - put,delete
To clear granted permissions on /foo/index.html for user1, type:
realm perm -w /myService -realm testRealm1 -s /myService/contexts/myContext -n user1 -u /foo/index.html +
To list all permissions for a user, type:
realm perm -w /myService -realm testRealm1 -s /myService/contexts/myContext -n user1
More Details
In the policy subcontext of a servlet context, there will be an entry, config. This is the entry used to create the object responsible for all permission declaration checks. Again, the object is used as a key into the permissions table, JAVA$HTTP$REALM$POLICY$
All HTTP Security is declared through JNDI namespace entries. This is also true for the servlet that does the enforcing of security. In the servlet context, if there is a PrivilegedServlet named httpSecurity, that servlet is added as the first pre-filter for all requests within that servlet context.
Any customization is allowed as long as the PrivilegedServlet interface is implemented.The main responsibility of this servlet is to either:
or
After authentication and authorization have taken place, the servlet must set specific authenticated principal values on the request itself. This is the user information that can be retrieved from the request by any executing servlet.
To create a security servlet, type:
realm secure -s /myService/contexts/myContext
There are several layers of suspected problems to eliminate when debugging HTTP Security. This minimal checklist can help you start your trouble shooting quest.
|
|
 Copyright © 1996-2000, Oracle Corporation. All Rights Reserved. |
|