Release 3 (8.1.7)
Part Number A83722-01
Library |
Product |
Contents |
Index |
| Oracle8i CORBA Developer's Guide and Reference Release 3 (8.1.7) Part Number A83722-01 |
|
The server can require a different type of authentication depending on its role. If you are utilizing the database as a server in a typical client/server environment, you use certificates that are set within a wallet for the database for server-side authentication. However, if you are using the server to callout to another object or callback to an object on the client, the server is now acting as a client and so requires its own identifying certificates. That is, in a callout or callback scenario, the server cannot use the wallet generated for database server-side authentication.
The following sections describe this in more detail:
Server-side authentication takes place when the server provides certificates for authentication to the client. When requested, the server will authenticate itself to the client, also known as server-side authentication, by providing certificates to the client. The SSL layer authenticates both peers during the connection handshake. The client requests server-side authentication by setting any of the SSL_* values in the JNDI property. See "Using JNDI for Authentication" for more information on these JNDI values.
For server-side authentication, you must set up a database wallet with the appropriate certificates, using the Wallet Manager. See the Oracle Advanced Security Administrator's Guide for information on how to create a wallet.
|
Note: If the client wants to verify the server against trustpoints or authorize the server, it is up to the client to set up its trustpoints and parse the server's certificates for authorization. See "Authorization" for more information. |
A callout is when a Java object loaded within the database invokes a method within another Java object. If the original call from the client required a certain level of security--certificate-based or username/password security--the server object is also required to provide the same level of security information for itself before invoking the method on the second server object.
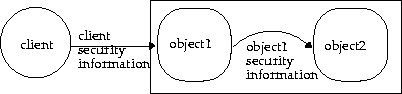
AuroraCertificateManager as discussed in "Using Certificates for Client Authentication".
A callback is when the client passes the server object an object reference to an object that exists on the client. As shown in Figure 6-3, the server object receives the object reference and invokes methods. This effectively calls out of the server and back to an object located in the client. See "Debugging Techniques" for more information on callbacks.
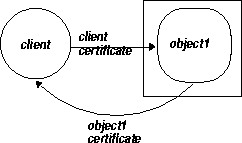
The type of security you can use for callbacks is certificate-based security over SSL. When you add SSL security to callbacks, you can have one of two situations:
The following code shows the client code that performs (a) and (d) steps above. The first half of the client code sets up a username and password for authenticating itself to the database. It retrieves the server object. However, before it invokes the server's method, the last half of the code sets up the client callback object by setting certificates, initializing the BOA, and instantiating the callback object. Finally, the server method is invoked.
public static void main (String[] args) throws Exception { String serviceURL = args [0]; String objectName = args [1]; String user = args [2]; String password = args [3]; //set up username/password for authentication to database. Set up //security to be SSL_LOGIN - login authentication for client and server-side //authentication. Hashtable env = new Hashtable (); env.put (Context.URL_PKG_PREFIXES, "oracle.aurora.jndi"); env.put (Context.SECURITY_PRINCIPAL,user); env.put (Context.SECURITY_CREDENTIALS,password); env.put (Context.SECURITY_AUTHENTICATION, ServiceCtx.SSL_LOGIN); Context ic = new InitialContext (env); // Get the server object before preparing the client object. // You have to do it in this order to get the ORB initialized correctly Server server = (Server)ic.lookup (serviceURL + objectName); // Create the client object and export it to the ORB in the client // First, set up the ORB properties for the callback object java.util.Properties props = new java.util.Properties(); props.put("ORBservices", "oracle.aurora.ssl"); BASE64Decoder decoder = new BASE64Decoder(); // Initialize the ORB. com.visigenic.vbroker.orb.ORB orb = (com.visigenic.vbroker.orb.ORB)oracle.aurora.jndi.orb_dep.Orb.init(args, props);// Get the certificate manager AuroraCertificateManager certificateManager =
AuroraCertificateManagerHelper.narrow( orb.resolve_initial_references("AuroraSSLCertificateManager")); // Set up client callbackcertificate chain, ordered from user to CA. byte[] userCert = decoder.decodeBuffer(testCert_base64); byte[] caCert = decoder.decodeBuffer(caCert_base64); // Set my certificate chain, ordered from CA to user. byte[][] certificates = { caCert, userCert };cm.setCertificateChain(certificates);cm.addTrustedCertificate(caCert); // Set client callback object's private key. byte[] encryptedPrivateKey=decoder.decodeBuffer(encryptedPrivateKey_base64);cm.setEncryptedPrivateKey(encryptedPrivateKey, "welcome12");// Initialize the BOA with SSLorg.omg.CORBA.BOA boa = orb.BOA_init("AuroraSSLTSession", null);//Instantiate the client callback object ClientImpl client = new ClientImpl (); //register callback object with BOA boa.obj_is_ready (client); // Invoke the server method, passing the client to call us back System.out.println (server.hello (client)); } }
The code for the client shown in Example 6-2 is the same for this scenario, except
that instead of providing a username and password, the client provides certificates.
Since client-side authentication is required and because the server is acting as a
client, the server code sets up identifying certificates for itself before invoking the
callback object. The server must create and send its own certificates, it cannot
forward on the client's certificates for authentication. You set up your server object
certificates using either the appropriate JNDI properties or the
AuroraCertificateManager as discussed in "Using Certificates for Client
Authentication".
The following server code does the following:
AuroraCertificateManager
AuroraCertificateManager methods.
hello.
public String hello (Client client) { BASE64Decoder decoder = new BASE64Decoder(); com.visigenic.vbroker.orb.ORB orb = (com.visigenic.vbroker.orb.ORB)oracle.aurora.jndi.orb_dep.Orb.init(); try { // Get the certificate manager AuroraCertificateManager cm = AuroraCertificateManagerHelper.narrow( orb.resolve_initial_references("AuroraSSLCertificateManager")); byte[] userCert = decoder.decodeBuffer(testCert_base64); byte[] caCert = decoder.decodeBuffer(caCert_base64); // Set my certificate chain, ordered from CA to user. byte[][] certificates = { caCert, userCert }; cm.setCertificateChain(certificates); // Set my private key. byte[] encryptedPrivateKey =
decoder.decodeBuffer(encryptedPrivateKey_base64); cm.setEncryptedPrivateKey(encryptedPrivateKey, "welcome12"); } catch (Exception e) { e.printStackTrace(); throw new org.omg.CORBA.INITIALIZE( "Couldn't initialize SSL context"); } return "I Called back and got: " +client.helloBack(); }
|
|
 Copyright © 1996-2000, Oracle Corporation. All Rights Reserved. |
|