Release 3 (8.1.7)
Part Number A85397-01
Library |
Product |
Contents |
Index |
| Oracle8i SQL Reference Release 3 (8.1.7) Part Number A85397-01 |
|
SQL Statements:
ALTER TABLE to constraint_clause, 10 of 14
Use the AUDIT statement to:
To audit occurrences of a SQL statement, you must have AUDIT SYSTEM system privilege.
To audit operations on a schema object, the object you choose for auditing must be in your own schema or you must have AUDIT ANY system privilege. In addition, if the object you choose for auditing is a directory object, even if you created it, you must have AUDIT ANY system privilege.
To collect auditing results, you must set the initialization parameter AUDIT_TRAIL to DB. You can specify auditing options regardless of whether auditing is enabled. However, Oracle does not generate audit records until you enable auditing.
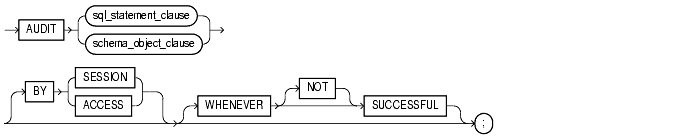


sql_statement_clause
|
|
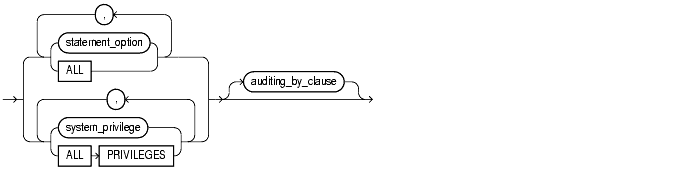
Specify a statement option to audit specific SQL statements. |
|
|
|
For each audited operation, Oracle produces an audit record containing this information: |
|
|
|
Oracle writes audit records to the audit trail, which is a database table containing audit records. You can review database activity by examining the audit trail through data dictionary views.
|
|
|
|
Specify a system privilege to audit SQL statements that are authorized by the specified system privilege.
|
|
|
|
Rather than specifying many individual system privileges, you can specify the roles CONNECT, RESOURCE, and DBA. Doing so is equivalent to auditing all of the system privileges granted to those roles.
|
|
|
|
Oracle also provides two shortcuts for specifying groups of system privileges and statement options at once: |
|
|
|
|
Specify |
|
|
|
Specify |
|
|
|
|
|
|
Specify the |
|
|
|
|
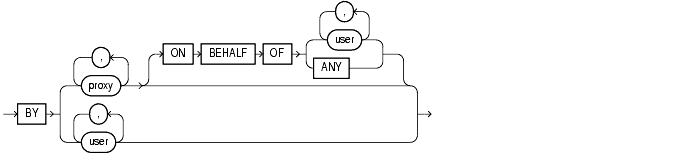
Use this clause to restrict auditing to only SQL statements issued by the specified users. |
|
|
|
Use this clause to restrict auditing to only SQL statements issued by the specified proxies.
|
|
|
|
|
schema_object_clause
|
|
Specify the particular operation for auditing. Table 8-3 shows each object option and the types of objects to which it applies. The name of each object option specifies a SQL statement to be audited. For example, if you choose to audit a table with the |
|
|
|
Specify |
|
|
|
The |
|
|
|
|
Specify the schema containing the object chosen for auditing. If you omit |
|
|
|
Specify the name of the object to be audited. The object must be a table, view, sequence, stored procedure, function, package, materialized view, or library. |
|
|
|
You can also specify a synonym for a table, view, sequence, procedure, stored function, package, or materialized view. |
|
|
|
Specify ON DEFAULT to establish the specified object options as default object options for subsequently created objects. Once you have established these default auditing options, any subsequently created object is automatically audited with those options. The default auditing options for a view are always the union of the auditing options for the view's base tables. You can see the current default auditing options by querying the |
|
|
|
If you change the default auditing options, the auditing options for previously created objects remain the same. You can change the auditing options for an existing object only by specifying the object in the ON clause of the AUDIT statement. |
|
|
|
The |
|
|
Specify |
|
|
|
Specify |
|
|
|
If you specify statement options or system privileges that audit data definition language (DDL) statements, Oracle automatically audits by access regardless of whether you specify the |
|
|
|
For statement options and system privileges that audit SQL statements other than DDL, you can specify either |
|
|
|
Specify |
|
|
|
Specify |
|
|
|
If you omit this clause, Oracle performs the audit regardless of success or failure. |
|
To choose auditing for every SQL statement that creates, alters, drops, or sets a role, regardless of whether the statement completes successfully, issue the following statement:
AUDIT ROLE;
To choose auditing for every statement that successfully creates, alters, drops, or sets a role, issue the following statement:
AUDIT ROLE WHENEVER SUCCESSFUL;
To choose auditing for every CREATE ROLE, ALTER ROLE, DROP ROLE, or SET ROLE statement that results in an Oracle error, issue the following statement:
AUDIT ROLE WHENEVER NOT SUCCESSFUL;
To choose auditing for any statement that queries or updates any table, issue the following statement:
AUDIT SELECT TABLE, UPDATE TABLE;
To choose auditing for statements issued by the users scott and blake that query or update a table or view, issue the following statement:
AUDIT SELECT TABLE, UPDATE TABLE BY scott, blake;
To choose auditing for statements issued using the DELETE ANY TABLE system privilege, issue the following statement:
AUDIT DELETE ANY TABLE;
To choose auditing for statements issued using the CREATE ANY DIRECTORY system privilege, issue the following statement:
AUDIT CREATE ANY DIRECTORY;
To choose auditing for CREATE DIRECTORY (and DROP DIRECTORY) statements that do not use the CREATE ANY DIRECTORY system privilege, issue the following statement:
AUDIT DIRECTORY;
To choose auditing for every SQL statement that queries the emp table in the schema scott, issue the following statement:
AUDIT SELECT ON scott.emp;
To choose auditing for every statement that successfully queries the emp table in the schema scott, issue the following statement:
AUDIT SELECT ON scott.emp WHENEVER SUCCESSFUL;
To choose auditing for every statement that queries the emp table in the schema scott and results in an Oracle error, issue the following statement:
AUDIT SELECT ON scott.emp WHENEVER NOT SUCCESSFUL;
To choose auditing for every statement that inserts or updates a row in the dept table in the schema blake, issue the following statement:
AUDIT INSERT, UPDATE ON blake.dept;
To choose auditing for every statement that performs any operation on the order sequence in the schema adams, issue the following statement:
AUDIT ALL ON adams.order;
The above statement uses the ALL shortcut to choose auditing for the following statements that operate on the sequence:
CURRVAL or NEXTVAL
To choose auditing for every statement that reads files from the bfile_dir1 directory, issue the following statement:
AUDIT READ ON DIRECTORY bfile_dir1;
The following statement specifies default auditing options for objects created in the future:
AUDIT ALTER, GRANT, INSERT, UPDATE, DELETE ON DEFAULT;
Any objects created later are automatically audited with the specified options that apply to them, provided that auditing has been enabled:
ALTER, GRANT, INSERT, UPDATE, or DELETE statements issued against the table.
GRANT, INSERT, UPDATE, or DELETE statements issued against the view.
ALTER or GRANT statements issued against the sequence.
ALTER or GRANT statements issued against it.
|
|
 Copyright © 1996-2000, Oracle Corporation. All Rights Reserved. |
|